Hoax-Slayer - Meta Scams, a 1954 Computer Hoax, and More!
Issue #3
Meta ‘Facebook Violation’ Phishing Scams
A few days ago, my wife received a “trademark violation” warning message, supposedly connected to one of her Facebook Pages. The message, which claims to be from Meta, warns that her Facebook Page will be deleted unless she clicks a link to request a review.
However, the message is not from Meta, and the threat to delete the page is a scam designed to trick people into giving their private information to criminals.
Link Opens Scam Website
If you click the link, you will be taken to a bogus website built to emulate the genuine Facebook website. Once on the fake page, you will be asked to enter your Facebook login credentials. After you “log in” on the fake page, you may be taken to a “review form” that asks you to provide your personal information.
All the information you submit on the fake site will be sent to criminals, who can use it to hijack your Facebook account and steal your identity.
Hijacked Accounts Used For Further Scams
Typically, scammers use your hijacked account to send further scam messages and promote their nefarious activities. It can be quite difficult to regain control of hijacked accounts.
Login Via Facebook App or Website
Be wary of any supposed “policy violation” or “account suspended” message or email that claims to be from Meta or Facebook. If you receive one, don’t click or tap any links that it contains.
Instead, log in to your Facebook account via the Facebook website or app. If the violation is a genuine warning, you will see a notification once logged in.
Many Variations
There are many versions of these scams, and online criminals have distributed them for decades. Other social media platforms, such as Instagram, are also regularly targeted.
Your sensitive personal information and your social media accounts are valuable prizes for criminals, and this old trick still works well for them.
A Screenshot of the Scam Message
An Older Version of the Same Scam
Here’s a short video showing another version of the scam from several years ago. As you can see, same scam, different year.
1954 Home Computer Hoax
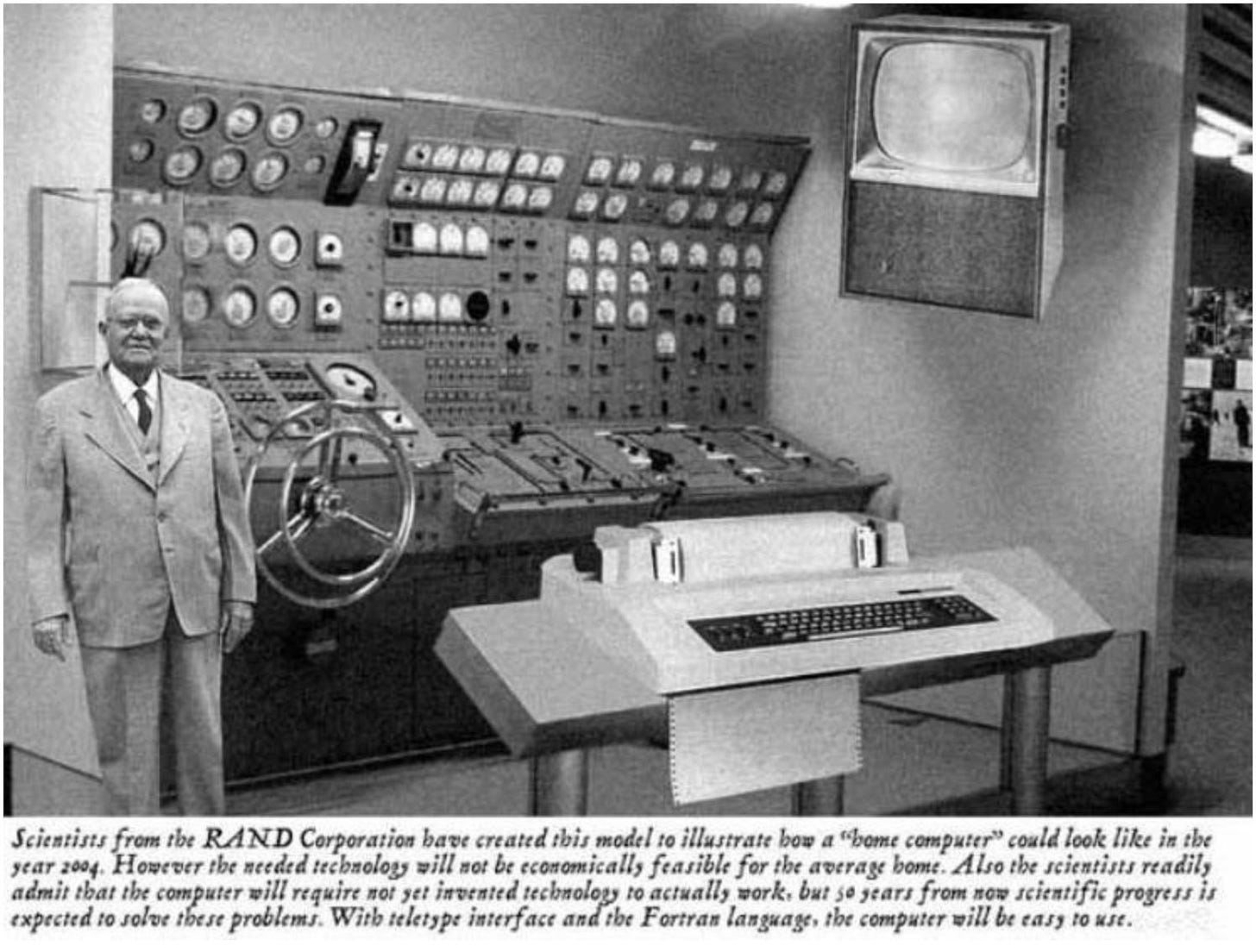
The caption accompanying this long circulated image claims that it depicts how scientists in 1954 imagined a home computer might look like in 2004.
The image has now been circulating for more than 20 years, first via email and forum posts and, in later years, via social media websites. Some versions assert that the image was included in a 1954 edition of “Popular Mechanics”.
The text below the image states:
Scientists from the RAND corporation have created this model to illustrate how a “Home Computer” could look like in the year 2004. However, the needed technology will not be economically feasible for the average home. Also the scientists readily admit that the computer will require not yet invented technology to actually work, but 50 years from now scientific progress is expected to solve these problems. With teletype interface and the FORTRAN language, the computer will be easy to use.
In fact, no such “Home Computer” model was ever created. Nor was the image published in any 1954 edition of “Popular Mechanics”. The image is the end result of some clever manipulation of a real photograph that depicts a full-scale mock-up of a typical nuclear-powered submarine’s maneuvering room:
The manipulated “home computer” image was an entry in a Photoshop competition organised by Fark.com. The entry was submitted by a Fark user posting under the name lukket.
The image has been accepted as legitimate by many people and has generated a lot of sometimes amusing debate. Some have postulated that the large wheel in the picture was intended to fulfil the function of the modern-day mouse. Others have pondered if a FORTRAN-based system with a teletype interface would really be that “easy to use”.
Editor’s note:
The images entered in the old Fark competition discussed in this article are no longer available on the site. The competition was launched back in 2004 and, not surprisingly, many of the entries posted are now listed on the site as “too old to be available”.
Why Do Otherwise Smart People Fall For Obvious Scams and Hoaxes?
Every day, thousands of Internet users fall for silly hoaxes and transparent scams. Why?
Many commentators suggest that all of the people who fall for such scams and hoaxes are just plain stupid. This is not true.
I’ve been working in the hoax and scam debunking field for more than twenty years, and during that time, I’ve talked to a great many people who have been scammed or who have fallen for hoaxes. And I can assure you that they are not always stupid. Many are smart, articulate, and well-educated.
So why do otherwise smart people fall for obvious scams and hoaxes? There is perhaps no clear and definitive answer, but here are a few ideas.
People Click Before They Think
The immediacy of social media is one of its strengths. But, it can also be one of its problems.
You can like or share something in an instant. A single click can take you to a dangerous website or open a malware attachment. In the blink of an eye, you can like and share a silly fake-news report that you’ve just glanced at, which promotes it across your networks.
Everything online seems to hurtle along at a frenetic pace. It’s easy for people to get caught in the moment and click away when, ideally, they should have stepped back and more closely analysed what they are reading. Applied some critical thinking, perhaps.
Information Overload
Hand in glove with the immediacy issue I discuss above goes information overload. These days, we are bombarded with information from many different directions at once. Email, blogs, forums, text messages, and, of course, continually updated social media feeds on Facebook, X, and other social networks.
And we receive an eclectic mix of many different types of information. Serious news and website articles, jokes, memes, updates from friends, business messages, images, spam, and much more. And scams and hoaxes as well.
In our efforts to process and manage this constant stream of information, we often tend to quickly scan much of what we receive, make instant decisions about it, and then move on to the next message.
Thus, at least for the few seconds that it takes them to scan a post, otherwise sensible people may believe that Facebook will donate money to help a sick child if they like and share. Or they may momentarily be taken in by a claim that they can win a luxury car or a vacation just by liking and sharing.
False Authority
Another positive aspect of the modern age is that virtually anybody can set up a website, blog, or social media page about any topic they like for free or for a minimal cost. Criminals and pranksters can misuse this ability.
It is easy to set up a fake website that closely mirrors the site of a high-profile company, government department, or celebrity. It is easy to create a blog that looks like a genuine news resource and fill it with nonsensical articles that appear to be real news reports. It is easy to set up fake Facebook Pages or X profiles that pretend to be associated with famous companies or people. It is easy to create and send scam emails that, at least at first glance, look like they were sent by companies like PayPal, Apple, or Amazon.
Unfortunately, it is also easy for busy, information-overloaded people to be taken in by such ruses and click, like, share, or download.
If fake information is presented with authority and looks legitimate at first take, it is incredible how many people will believe it.
New and Constantly Changing Technology
We often take our computers, our smartphones and tablets, and the wonderful world of the Internet for granted.
This technology has become an integral part of our everyday lives. Tech changes rapidly. New high-tech gadgets and new ways of doing things online are emerging all the time. AI is infiltrating itself into just about everything we do and, again, changing the online landscape.
It is easy for people to get lost within this heady and constantly changing tech landscape. Because such technology is purposefully designed for easy and intuitive use, people can use it to achieve their desired tasks without actually knowing too much about how it all works.
For example, a person may be quite proficient at using email, surfing the web, communicating on social media, and performing a host of other everyday computing tasks. But, he or she may have very little working knowledge of what malware is, how it infects computers, and what to do to prevent such infections.
Unlike a car or other types of machinery, computers and smartphones don’t require an operators licence, and we are not required to perform any formal training to start using them. We can dive in and go for it. But, gaps in our knowledge can sometimes leave us vulnerable to various types of online skulduggery.
The baffling gullibility of users can certainly be frustrating. It is easy to throw your hands in the air and give up trying to educate people.
Of course, we probably all know a few people who, despite constant warnings from their friends and family, continue to fall for every scam and nonsense post that comes their way. These serial victims tend to be the ones we all know and talk about.
But we should not judge all scam and hoax victims by these people. Many people only need a bit of guidance to set them right and give them the knowledge they need to avoid getting caught in the future.
And, if we do give up, the scammers and the malicious pranksters are the ones that end up winning.
Here’s What Happens When You Click a Phishing Link
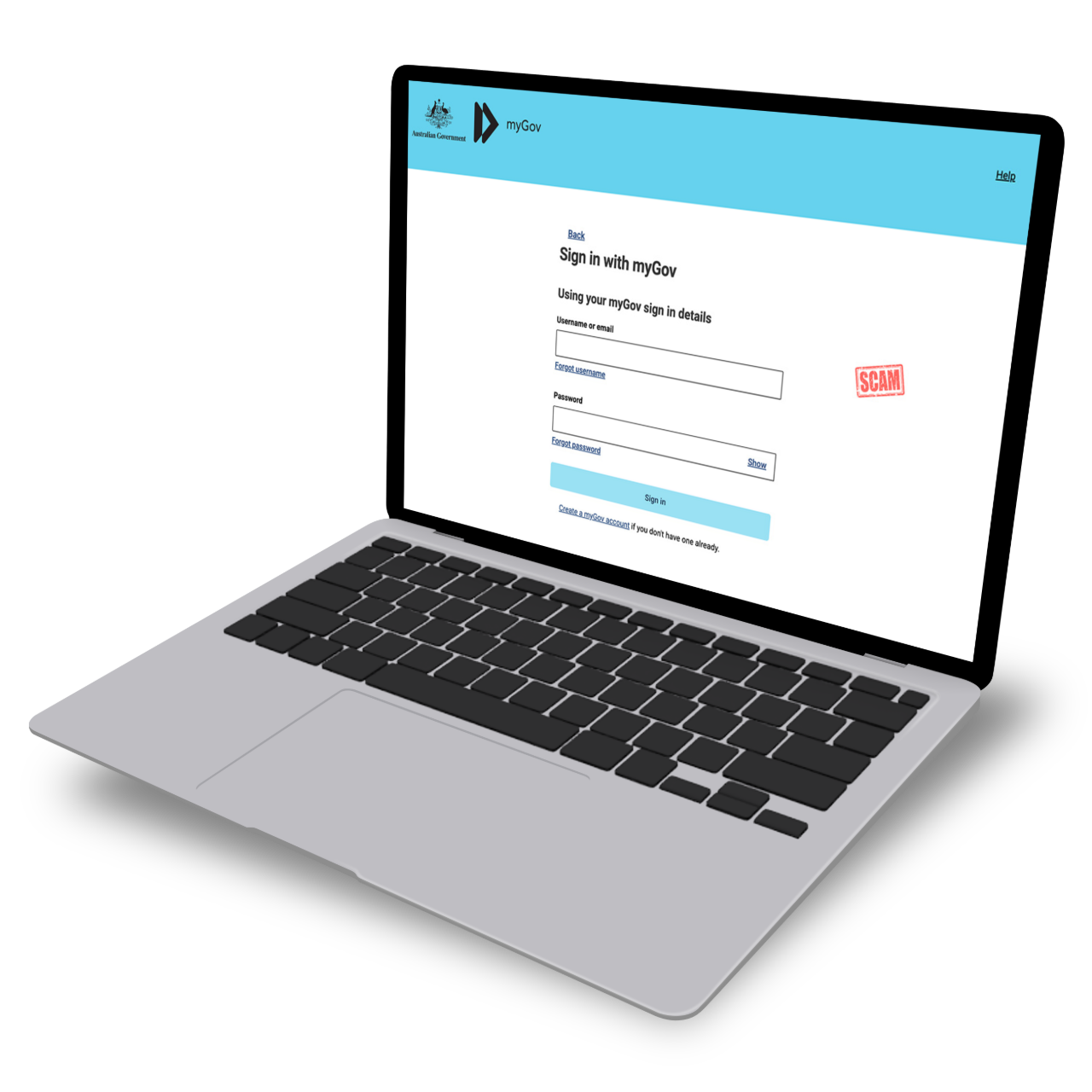
This is a typical phishing scam email that pretends to be from the Australian government portal MyGov. MyGov allows Australians to access various government services such as tax and social services:
Clicking the link takes you to a scam website that has been built to look almost exactly like a genuine MyGov page. The fake site asks you to sign in with your username and password.
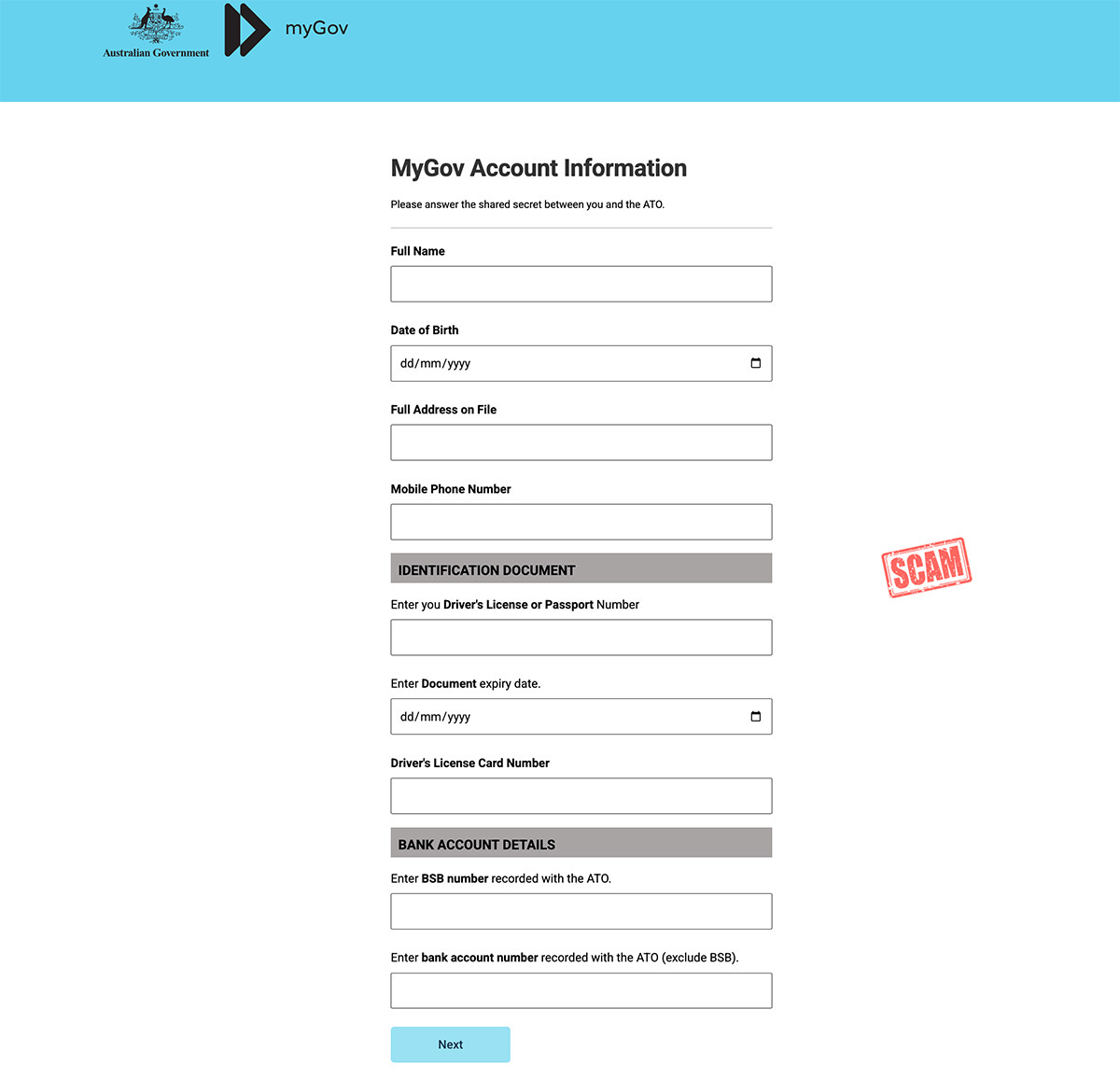
Once you sign in, you will be asked to fill in a fake form that asks for a large amount of your personal and financial information:
All of the information you provide will be sent to the criminals running the scam. They can use this information to steal your identity and hijack your MyGov account.
Also, since they now have your mobile phone number and other identifying information, the crooks can target you in further scams. For example, if you use two-factor authentication to protect your account, they may be able to trick you into sending them the SMS code so they can get into MyGov with the credentials you previously supplied.
Always access your online accounts by entering the address into your browser or via an official app. Don’t click links in emails or text messages.